Recent searches
Search options
#tls
About a third of the WWW #TLS traffic is using post-quantum encryption, which is protected against quantum factoring attacks such as Shor's algorithm. This has been achieved since Hybrid ML-KEM has been widely adopted by most web browsers and large service providers such as Cloudflare, Google, AWS, etc. There are no absolute figures available, but for example, Cloudflare has nice statistics about PQ encryption use on their services: https://radar.cloudflare.com/adoption-and-usage#post-quantum-encryption-adoption
The best part of this adoption is that users haven't had to do anything, or even know that this has been happening. As it should be.
@jeremiah_ @elb #NNCPNET, the new #NNCP-based email network, now has a bidirectional, opt-in, Internet #email bridge! https://salsa.debian.org/jgoerzen/docker-nncpnet-mailnode/-/wikis/bridge/intro
This gates Internet email to/from NNCP. The bridge is off by default. It is a full participant in #SPF, #DKIM, #DMARC, and #TLS in both directions.
Yes, now you can get Internet email straight to your #RaspberryPi ! (And even without this, your Pis can email each other!)

Revamping Web PKI: The Push for Shorter Certificate Validity and Data Reuse Periods
The ongoing evolution of the Web Public Key Infrastructure (PKI) is crucial for enhancing internet security. Recent proposals to shorten certificate validity and data reuse periods aim to address exis...
In the hope that someone here knows more Java than .. asking for a friend ... or something:
Is there a way to get more information from #Java when outbound #TLS connections fail (trust issues, for example)? And I do not want to enable debugging in the JVM; that would give me gigabytes of logs per second (yes, really). I basically want the application to make a connection, see it fail, and then handle that exception cleanly while also picking up precisely what the error was: Unknown CA, expired certificate, invalid usage flags, etc.
I'm clearly not a Java developer, just a sysadmin who is really frustrated with the extremely unhelpful Internet right now. I really don't need to be told "just turn off validation" or "just use ...javax.net.debug".
#OpenSSL 3.5.0 (#LTS) has been released (#SSL / #TLS) https://openssl-library.org/
OpenSSL 3.5.0 kennt Server-Side-QUIC und unterstützt PQC-Algorithmen - LinuxCommunity

Released: #swad v0.1
Looking for a simple way to add #authentication to your #nginx reverse proxy? Then swad *could* be for you!
swad is the "Simple Web Authentication Daemon", written in pure #C (+ #POSIX) with almost no external dependencies. #TLS support requires #OpenSSL (or #LibreSSL). It's designed to work with nginx' "auth_request" module and offers authentication using a #cookie and a login form.
Well, this is a first release and you can tell by the version number it isn't "complete" yet. Most notably, only one single credentials checker is implemented: #PAM. But as pam already allows pretty flexible configuration, I already consider this pretty useful
If you want to know more, read here:
https://github.com/Zirias/swad
DDoS Attacks (HTTP/2, DNS, Hacktivist)
This is Real World Technical Analysis
YouTube video: https://youtu.be/t2jKcA1OyBE
#Sponsored #cybersecurity #ddos #dos #DNS #http #tls #hack #hacker #hacking #cyber #internet Radware
Folien vom Dozenten: "Sicherheit: Datenübertragung mit SSL-Protokoll"
Ich will hoffen, dass er TLS und nicht SSL meint
System Administration
Week 8, HTTPS & TLS
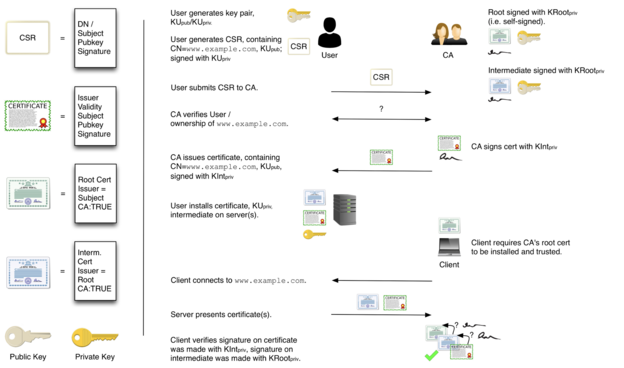
After discussing HTTP in the previous week and seeing how we used STARTTLS in the context of #SMTP, we are now quickly reviewing HTTPS, TLS, and the WebPKI. While we don't have a video segment for this, here are slides, including this handy diagram illustrating the CSR process:
Hat hier wer Connections zur IT-Abteilung von aok.de? Die haben gestern das SSL-Zertifikat ihres mx1.aok.de getauscht, aber den TLSA-Record für DANE übersehen...
https://dane.sys4.de/smtp/service.bw.aok.de
20:00 Uhr: geht wieder! Danke :)
Join Sake Blok for his pre-conference class at SharkFest'25 US on June 16th:
"SSL/TLS Troubleshooting with Wireshark"
This hands-on session will take your troubleshooting skills to the next level, helping you diagnose complex network issues like a pro.
Secure your spot: https://sharkfest.wireshark.org/sfus
System Administration
Week 8, The Simple Mail Transfer Protocol, Part II
In this video, we observe the incoming mail on our MTA, look at how STARTTLS can help protect information in transit, how MTA-STS can help defeat a MitM performing a STARTTLS-stripping attack, and how DANE can be used to verify the authenticity of the mail server's certificate.
This morning I spent some time debugging an app which logs as if it's AD 57203, to wit
{"level":20,"time":1742987150412,"pid":1, ...
$ date -r 1742987150412
Fri Jan 24 10:20:12 CET 57203
but it turns out the other instance (the one that works, as in the user is able to download files from there) has roughly the same time internally, so *that* was not its main problem.
Mind boggled, debugging to continue until *something* improves.
So after listening to your feedback, I agree: let’s spend that money in the EU to create a publicly-owned, free and open ACME-compatible certificate authority.
See post quoted below, with links to Tom’s work as he’s already been thinking/working on this.
#EU #ACME #TLS #security #LetsEncrypt #technologyCommons #SmallTech https://mamot.fr/@tdelmas/114224564125819333
Let’s Encrypt at risk from Trump cuts to OTF: “Let’s Encrypt received around $800,000 in funding from the OTF”
Dear @EUCommission, get your heads out of your arses and let’s find @letsencrypt €1M/year (a rounding error in EU finances) and have them move to the EU.
If Let’s Encrypt is fucked, the web is fucked, and the Small Web is fucked too. So how about we don’t let that happen, yeah?
(In the meanwhile, if the Let’s Encrypt folks want to make a point about how essential they are, it might be an idea to refuse certificates to republican politicians. See how they like their donation systems breaking in real time…)
CC @nlnet @NGIZero@mastodon.xyz
#USA #fascism #OpenTechFund #LetsEncrypt #SSL #TLS #encryption #EU #web #tech #SmallWeb #SmallTech https://mastodon.social/@publictorsten/114223873439053263
After mulling over how to use SSL within a LAN in a way that I felt really satisfied with, it took me well over 20 years! Did that ever take a long time.
#SelfHosting #TLS #SSL #web #infosec
I highly recommend Mosquitto and MQTTX as #opensource options for #mqtt broker and GUI client. They are great for setting up and testing home #IoT networks! Both work with CA-signed or self-signed certificates for #TLS connections, which is imperative for better #CyberSecurity.